At the AVAR Conference in November 2014, McAfee Labs presented how to exploit a cross-site scripting vulnerability of the Costco and Walgreens apps on Android. We shared with our audience research on other app vulnerabilities because we believe apps (especially mobile apps) will be an increasing attack surface for cybercriminals. Today we’d like to provide an update to this issue concerning insufficient transport-layer protection.
This topic covers similar ground to the stats McAfee called out last year in the McAfee Mobile Security Report: “After analyzing the behavior and permissions of thousands of Android apps, our research team found that 82% of apps track mobile activities,” the report said. When this type of data collection is sent to the app developer’s server without proper encryption, users’ personal information and enterprise data are at risk.
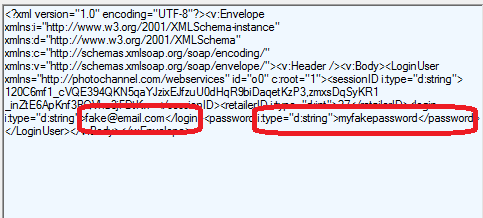
Costco app: naked credentials
The Android apps we analyzed in our AVAR paper are also exposed to this vulnerability. When we tested the Costco app with a fake account, the login request was clearly captured in Fiddler because the request was in plain HTTP. What does this mean? Be more cautious if you are shopping online using your phone while connecting to a public wireless network.
Motivated to discover similar risks in other apps, we tested a few more programs in depth and became very alarmed. This plain HTTP risk is everywhere. Let’s walk through two such apps, Weibo and Sogou.
Weibo: social media chat easily sniffed or spoofed
Weibo is a Chinese social media platform like Twitter or Facebook. You post your status, chat with your friends, etc. Now suppose you post a message as follows in Weibo:
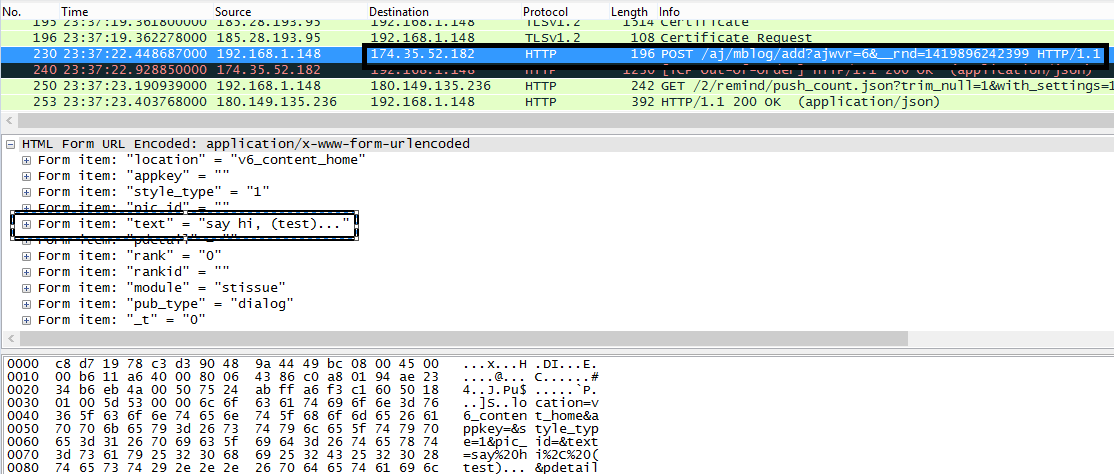
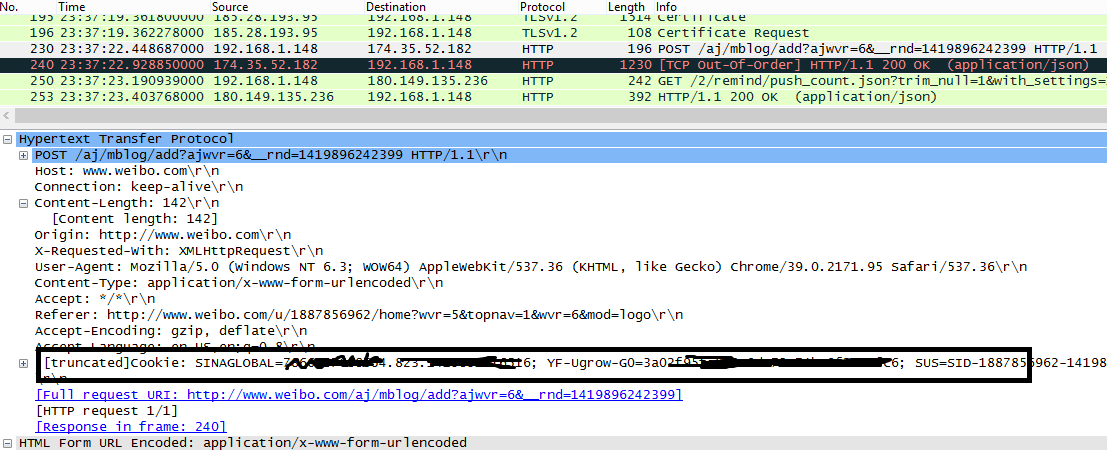
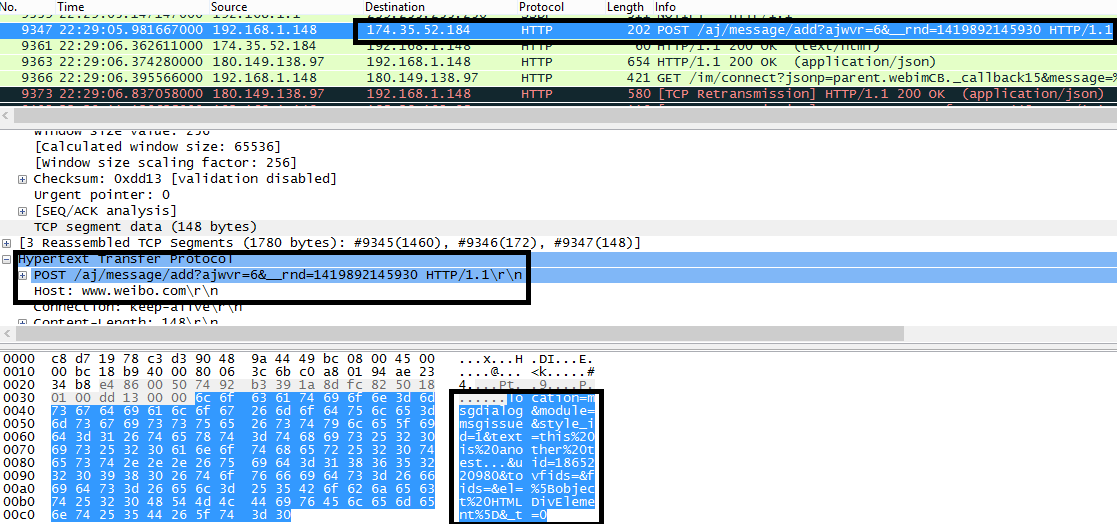
You can see what’s being sent to the Weibo backend by capturing the traffic from Wireshark:
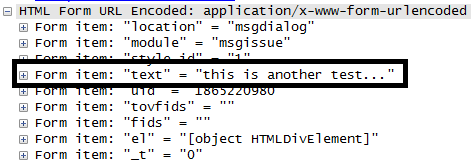
And the cookie is there for an attacker to harvest or even alter your post message via a man-in-the-middle attack.
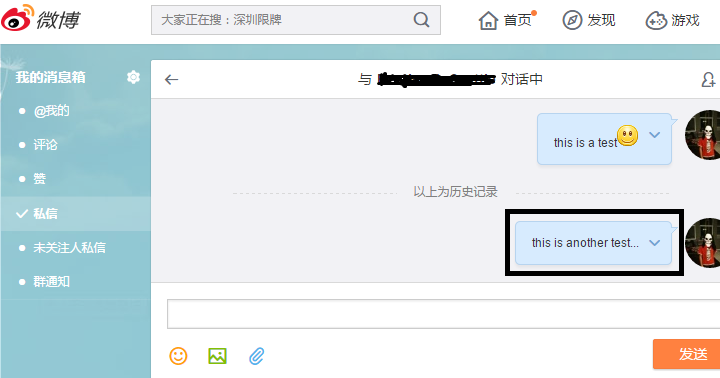
You may ask Who cares? This is a post on social media and is meant to be public. But what about your private chats with friends? We sent the following message via the chat window:
Again Wireshark shows us exactly the text, without encryption, begging for an attack (such as modifying the chat, injecting malicious links, etc.). There’s no privacy here!
Sogou sends device data via plain HTTP
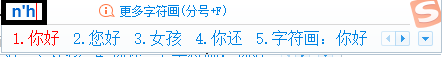
Sogou is the most popular Chinese input-method editor, claiming more than 400 million installations. Users benefit from hints to optimized words without having to fully spell them out in Pinyin). (Instead of typing ni hao for “hello”, for example, you type just “nh.”)
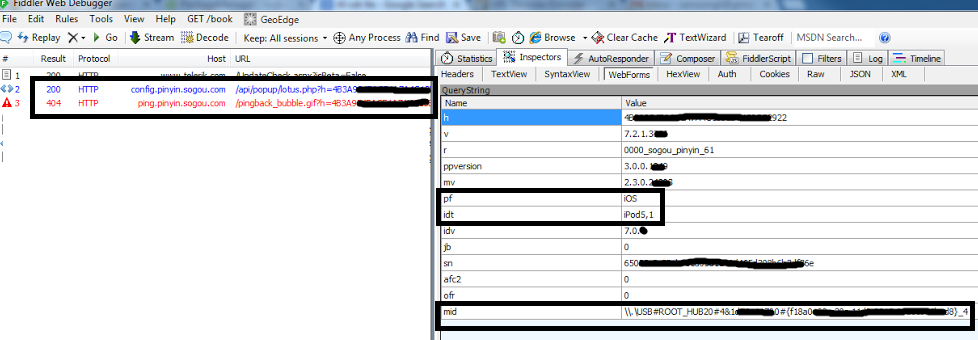
That’s all we want from a language input editor, and that’s why we installed it on a Windows 7 machine. However, when we connected an iPod via USB to this machine, we saw the following captured on Fiddler:
At first glance the preceding data may not seem like much, but it leads to a question: Why would a language input editor want to know “the user has connected an iOS device (iPod5), it is running on iOS 7.0, the serial number is “650…,” and it is connected via the USB hub “USB#ROOT_HUB20#48…”?
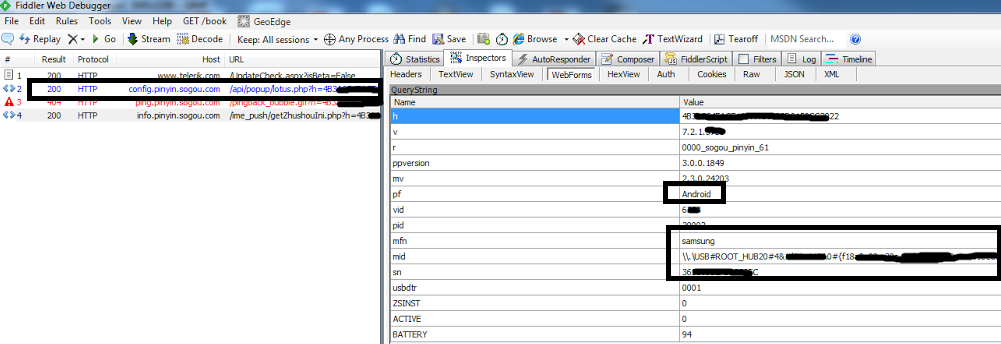
When we connected an Android phone, Fiddler showed a similar data collection:
Collecting device information in these scenarios is not something we expect or appreciate from language-input software. What is scarier is that the plain-HTTP transport invites attacks in the world full of poisoned mobile hotspots.
We call for app developers to close loopholes like these in their security development life cycles.